Walkthroughs
I just started creating these, but I’ll be adding more as I stumble across more challenging rooms!

Try Hack Me's Splunk 2 Room
Based on Splunk’s Boss of the SOC Ver. 2 (BOTSv2) competition
300 Series
1. Mallory’s critical PowerPoint presentation on her MacBook gets encrypted by ransomware on August 18. What is the name of this file after it was encrypted?
This answer pops up instantly after searching for Mallory and powerpoint extensions:
index=”botsv2″ mallory .pptx
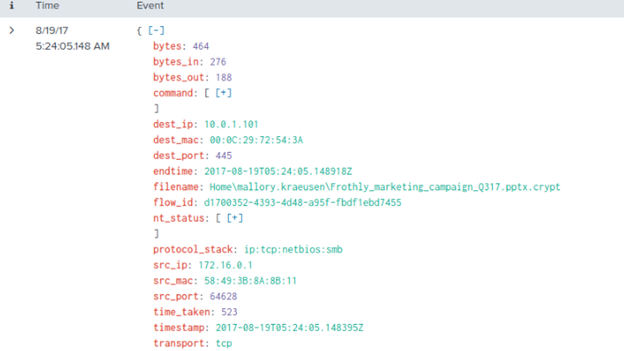
Note that the ransomware changes all affected files to end in .crypt.
2. There is a Games of Thrones movie file that was encrypted as well. What season and episode is it?
If it had been said that there was an episode of an unspecified TV show, it may have been helpful to try searching popular video file extensions (.mp4, .avi, etc.). Because we were told the show is Game of Thrones, we can add “Game of Thrones” or the popular abbreviation “got” to see what comes up (also searching for the .crypt extension):
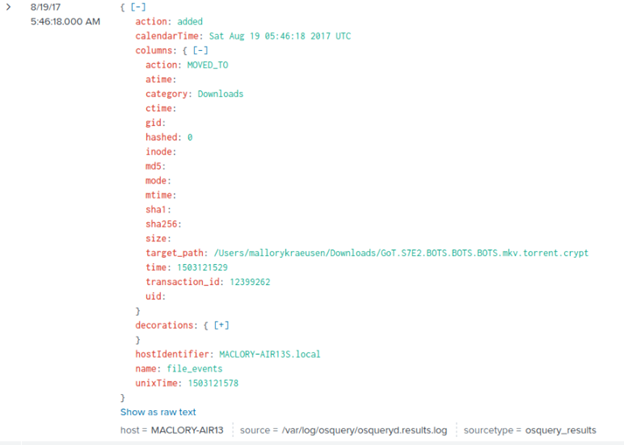
index=”botsv2″ .crypt got
And once again, the first event that comes up has our answer!
3. Kevin Lagerfield used a USB drive to move malware onto kutekitten, Mallory’s personal MacBook. She ran the malware, which obfuscates itself during execution. Provide the vendor name of the USB drive Kevin likely used. Answer Guidance: Use time correlation to identify the USB drive.
By looking around the logs for Mallory’s MacBook, “kutekitten”, we can find her folder pathnames, then pry further into them. Use index=”botsv2″ kutekitten | stats count by columns.path to see possible paths. Let’s look into her User folder (use double escape slashes to allow the slashes in the file path to be read correctly).
index=”botsv2″ kutekitten “\\/Users\\/mkraeusen”
This returns a lot of results, but the name field offers values that can narrow these results down significantly.
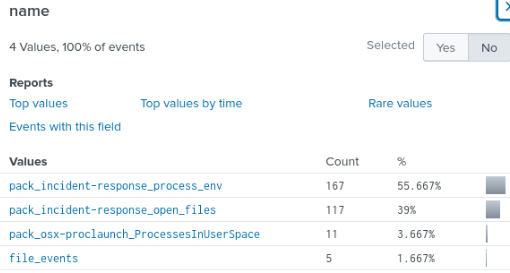
file_events sounds promising, so we’ll look into that.
index=”botsv2″ kutekitten “\\/Users\\/mkraeusen” name=file_events
The columns.sha256 field is available, and shows a hash that we can search on VirusTotal.com:
befa9bfe488244c64db096522b4fad73fc01ea8c4cd0323f1cbdee81ba008271
Because VT is flagging this as malicious, we can read some the other tabs to see what kind of malware is on the system. Keep this VT page up for now.
Back to the logs – filtering by the SHA-256 value shows two events at 6:19:07 PM on 8/3/2017:
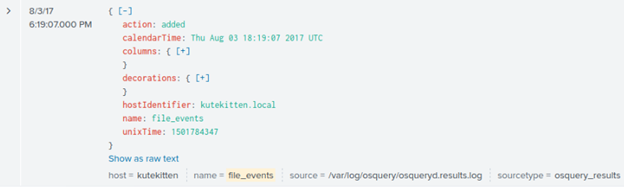
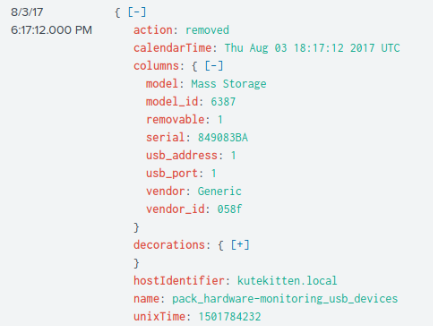
By focusing on all logs on Mallory’s computer within the 2-minute window before this event, we see that some logs have name = pack_hardware_monitoring_usb_devices, which seems likely to contain information about the device used to transfer the malware, so we apply that as a filter:
index=”botsv2″ kutekitten name=”pack_hardware-monitoring_usb_devices”
The results returned have the field columns.vendor_id . By searching these numerical ID’s on devicehunt.com, we will get our flag.
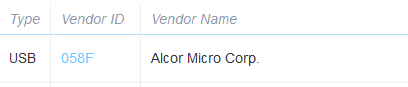
Questions 4-7 can be answered by looking through the VirusTotal page we pulled up earlier.
400 Series
Coming Soon!
